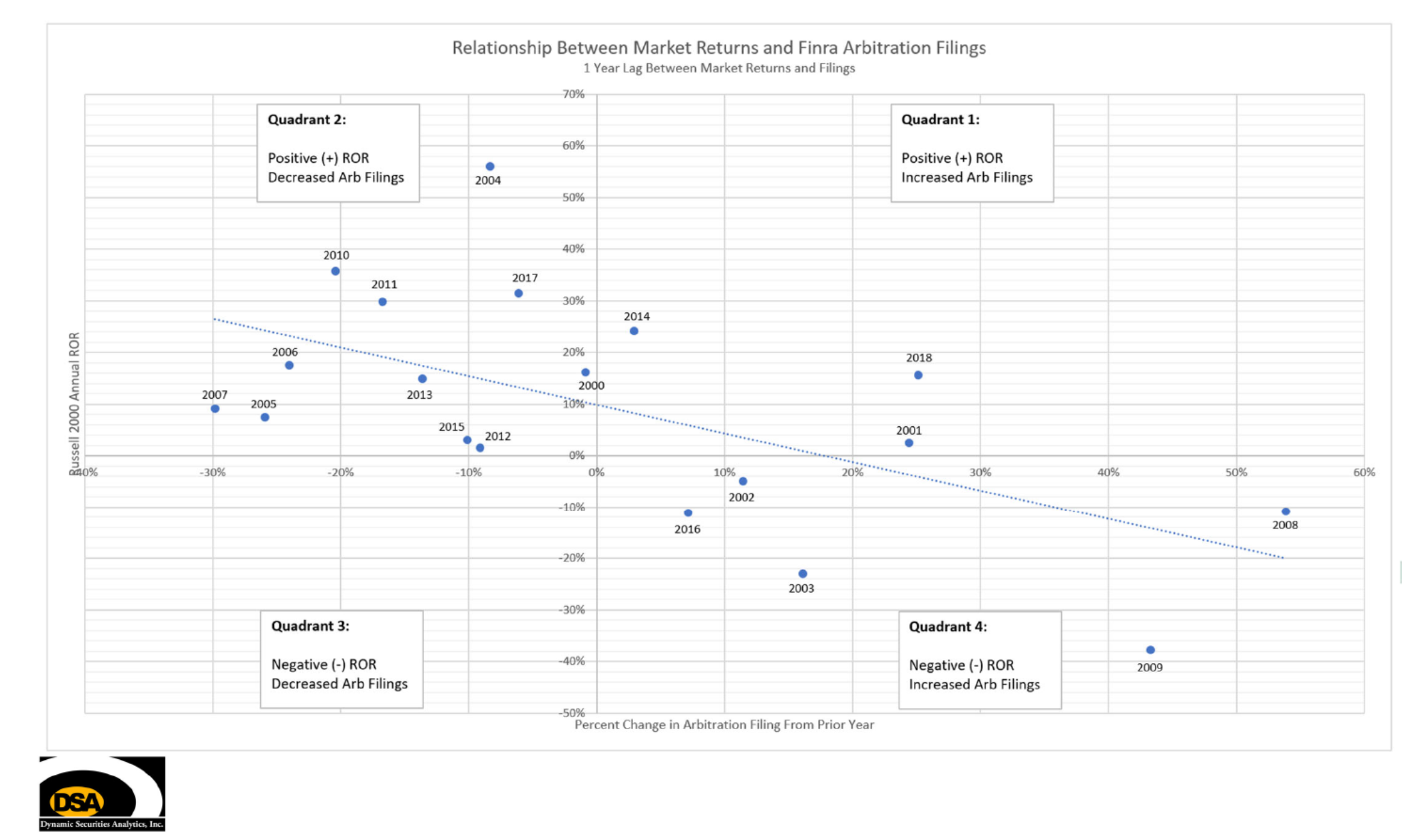
The Take-Away: Cryptocurrency crime estimates are often misunderstood. Learn what transactions and crimes are and are not included in the estimates. See 5/5/2022 update below.
Blockchain analytics companies such as Chainalysis, CipherTrace and Elliptic routinely publish cryptocurrency crime estimates. The reports are interesting and provide needed insight.
However, news articles and commentators often misunderstand what is and is not included in the cryptocurrency crime estimates. Misunderstanding the estimates can lead to faulty conclusions about the prevalence or rarity of cryptocurrency in illicit activity.
Top 3 Misconceptions about Cryptocurrency Crime Estimates
#1
Misunderstanding: Estimates Reflect All Cryptocurrency Crime
Reality: Estimates only Include Known Criminals and Crimes
Attribution is a key feature of blockchain forensic tools. Blockchain analytics companies have invested in staff and AI to try to assign a person, organization or entity to a given wallet address. When the blockchain analytics companies are able to attribute a wallet address to a ransomware attack or darknet market, the value of these transactions is included in the cryptocurrency crime estimate.
But there are plenty of crimes that escape attribution.
Here are a few examples:
- A ransomware payment that is not public (and did not use the same wallet addresses as prior known events)
- A bribe to a government official paid by a contractor directly from one wallet to another
- Remitting drug sale proceeds across borders for an organized drug cartel directly from one wallet to another
Paul Marrinan explained the issue of “known crimes” in his Crypto-crime & Caveats article:
The infinitesimal size of illicit activity which these reports can reliably identify is simply an indicator of analysis based on non-random events, as was recently cited in a peer-reviewed study. It is reasonable to assume that these reports do not account for a significant “dark figure of crime”, which has either not been detected or not been reported so far.
It is not that the blockchain analytics companies don’t spell out this limitation, it’s that people don’t pick up on it.
For instance, Chainalysis noted in its 2022 Preview Crypto Crime report:
As always, we have to caveat this figure and say that it is likely to rise as Chainalysis identifies more addresses associated with illicit activity and incorporates their transaction activity into our historical volumes. For instance, we found in our last Crypto Crime Report that 0.34% of 2020’s cryptocurrency transaction volume was associated with illicit activity – we’ve now raised that figure to 0.62%.
The Wall Street Journal further explained:
In its report, Chainalysis warns that its tracked volume of illicit activity is likely to rise later as the company identifies more bad actors and incorporates data gained from that into its historical analysis.
Chainalysis initially reported that just under $5 billion in cryptocurrency value was received by illicit entities in 2020. The 2020 crime estimate grew to $7.88 billion in their most recent report.
#2
Misunderstanding: Cryptocurrency Crime Estimates Include All Transactions
Reality: Estimates Exclude Illicit Transactions within Exchanges
A misconception often repeated by the media is that “all transactions are recorded on the blockchain.” Cryptocurrency exchanges match transactions among their own customers or from their own pool of coins/tokens. These internal transactions are not reported on the blockchain.
Cryptocurrency exchanges report transaction values magnitudes greater than what is recorded on the blockchain. Researchers estimate that off-chain Bitcoin transaction volume is at least 10 times greater than the on-chain transaction volume.
Reinhart, Rogoff & Graf von Luckner note that most quantitative research into illicit use of Bitcoin:
Have only been applied to on-chain transactions, that is, those that are immutably registered on the blockchain.
On-chain transactions, however, constitute only a small share of the universe of all Bitcoin trades, most of which are “off-chain” utilizing some form of exchange, some heavily regulated, some not so much.
Internal transactions at cryptocurrency exchanges are recorded on private ledgers. Reinhart et al noted that “the vast majority of off-chain transactions are proprietary information.” Other types of bitcoin transactions such as those on the Lightning Network as also not recorded on the blockchain. Therefore, cryptocurrency crime estimates that only consider on-chain transactions reflect a small fraction of crypto transactions.
Some might suggest that since cryptocurrency exchanges are supposed to be regulated, it is not important to know what is happening inside exchanges. However, just as banks, broker-dealers, and traditional MSBs are often the venue of criminal and layering transactions, so too are cryptocurrency exchanges.
Law enforcement clearly sees value in understanding what happens within cryptocurrency exchanges. Coinbase reported that in the first half of 2020, it received more than 1,800 law enforcement criminal requests for information. The FBI accounted for the largest share of criminal information requests. The Coinbase Transparency Report Q1-Q3, 2021 reported that the company received 5,174 criminal information requests.
FinCEN received approximately $119B in suspicious activity reporting involving CVC in 2019. FinCEN noted that much of this figure occurred prior to 2019 and was detected via lookbacks. The $119B figures is at least ten times the amount identified in the crime estimates for 2019. This could partially be due to cryptocurrency exchanges having insight into potentially criminal activity occurring within their firm (i.e. not on the blockchain).
#3
Misconception: Money Laundering is Included in Cryptocurrency Crime Estimates
Reality: Estimates Exclude Layering Transactions
It appears that only the initial “illicit activity” received is counted in the blockchain analytics cryptocurrency crime estimates.[1] Yet, it is common for criminals to layer transactions through tens, hundreds and even thousands of wallets to make it more difficult to trace.
Elliptic noted:
You do not need to provide your identity when creating a wallet, and you can easily create thousands or millions of wallets, in seconds.
Money launderers have exploited this to layer cryptoassets through hundreds of wallets using automated processes. This essentially mimics the fiat method of blurring or obfuscating the trail back to the original illicit source of funds.
Consider the following example:
Company A paid $300,000 worth of bitcoin to a wallet for a ransomware ransom.
Ransomware Organization B layered the $300,000 through twenty different wallets, for the total value of all transactions involving the illicit funds of $6,000,000.
The cryptocurrency crime estimates would include the $300,000 ransom payment but exclude the $5,700,000 in layering transactions of the ransom payment.
Some folks might argue that the initial criminal activity is what is important. Again, if a bank was to argue that it wasn’t important to identify layering transactions, I think they would get pushback from their regulator.
Chainalysis cryptocurrency crime estimate refers to “scamming revenue” and “cryptocurrency theft” which suggests that they only count the initial criminal activity and exclude the layering transactions from the $14.08B illicit activity estimate for 2021. Similarly, CipherTrace sums the value of hacks and thefts but does not provide a value of all the layering transactions for the stolen funds.
By excluding the value of the layering transactions, the cryptocurrency crime estimates implies that the layering transactions values are licit. Yet layering is literally the definition of money laundering.
Researchers such as Sean Foley has taken a broader approach to estimating illicit cryptocurrency transaction volumes. Also see Paul Marrinan’s article dissecting crypto-crime data.
To hear another perspective on cryptocurrency crime estimates, read Jim Richard’s Crypto vs. Fiat article.
Problematic Comparisons

The cryptocurrency crime reports often contain a comparison against the total dollar value of all crypto transactions.
For example, CNBC reported:
Transactions involving illicit addresses represented an all-time low of just 0.15% of the $15.8 trillion in total crypto trade volume in 2021.
This compares apples and oranges. The “apple” being the initial crypto crime being counted once (or perhaps twice–see footnote), yet the “orange” includes all transactions including the thousands of layering transactions. A more accurate ratio would compare the total dollar value of all illicit transactions, including the layering/obfuscation transactions against the “total crypto trade volume”.
UPDATE: 5/5/2022
I had the pleasure of speaking with Kim Grauer, Head of Research at Chainalysis. She helped clarify a few points on how Chainalysis calculated the 0.15% number above. Kim explained that Chainalysis tries to isolate economically meaningful transactions by backing-out peel chains, UTXO, and other transactions where the illicit actor moved value without changing ownership/control.
Using the $300,000 ransomware example above, the illicit numerator would be $300,000 and the denominator would also be $300,000 after backing-out the transactions that did not change ownership/control.
However, there seems to be a few ways that the denominator can still be inflated by pumping the “total transaction value”. First, if an illicit actor moves funds from their wallet to an exchange and then out of the exchange into another wallet or exchange, these transaction values would not be backed-out because (generally) you can’t trace through a cryptocurrency exchange.
Second, Chainalysis is rightly focused on illicit actors but plenty of licit wallets move huge amounts of crypto without changing ownership. It does not sound like the licit but “non-economically meaningful” transactions are backed out of the denominator.
Research by Igor Makarov and Antoinettte Schoar found:
90% of transaction volume on the Bitcoin blockchain is not tied to economically meaningful activities but is the byproduct of the Bitcoin protocol design as well as the preference of many participants for anonymity….
Many bitcoin users adopt strategies designed to impede the tracing of bitcoin flows by moving their funds over long chains of multiple addresses and splitting payments among them resulting in a large amount of spurious volume.
Despite the limitations, the cryptocurrency crime analyses provided by blockchain analytics companies are worth the read.
Here are a few resources to get you started:
Chainalysis Preview: 2022 Crypto Crime Report
CipherTrace Cryptocurrency Crime and Anti-Money Laundering Report, August 2021
Elliptic 2022 DeFi Risk, Regulation and the Rise of DeCrime
Want more Cryptocurrency Insights?
Read DSA’s analysis on Unregistered Cryptocurrency Exchange SARs.
Read DSA’s analysis on Cryptocurrency SARs: What do we know?
[1] The cryptocurrency crime estimates prepared by blockchain analytics firms do not provide detail on how exactly the estimates were calculated.
For example, Chainalysis refers to “Total Funds Received by Illicit Entities” for the headline-grabbing number of $14.8B in cryptocurrency crime. The 2020 report contains a graph totaling the “cryptocurrency value sent and received by illicit entities”.
* 5/5/2022: It would be interesting to know for every $X dollar of illicit proceeds earned, that the proceeds were layered Y times (via non-economically meaningful transactions). For example, does $1,000 in illicit proceeds spawn $10,000 of crypto blockchain transactions or $1,000,000?