FinCEN Warns of Real Estate Business Email Compromise
Alison Jimenez, DSA president, was recently quoted in a moneylaundering.com article by Benjamin Hardy on FinCEN’s recent Real Estate Business Email Compromise (‘BEC’) advisory.
FinCEN reviewed 2,300 suspicious activity reports from 2020 and 2021 involving business email compromise attacks against the real estate industry and customers. The flagged transactions totaled nearly $900 million.
Alison Jimenez, president of Dynamic Securities Analytics in Florida, said BEC real estate scammers sometimes hack into the emails of everyday people– rather than those of real estate professionals– then scan them for mentions of terms such as “mortgage,” “loan” and other keywords that may indicate a high-value transaction is imminent.
Bad actors send out emails with fake wiring instructions and also intercept legitimate emails and delete & replace the payment instructions.
Business Email Compromise Scammers Involved in Other Fraud Schemes
FinCEN’s trend analysis found that real estate BEC scammers have used the same bank accounts to launder funds as PPP Fraud, Romance Scams, and Unemployment assistance fraud.
AML professionals should not view the above crimes in silos, since the Transnational Criminal Organizations running these schemes do not.
For example, a romance scam victim may serve as an unwitting money mule for a BEC incident. The virtual boyfriend/hacker engenders trust by first sending (stolen) BEC money to the romance victim’s bank account. The romance scam victim then helps their ‘friend’ by conducting a second transaction (ex. wiring to a foreign country, sending funds to a cryptocurrency exchange, or buying gift cards). The romance scam victim is then convinced to send their own money to the scammer.
Transnational Criminal Organizations & Business Email Compromise
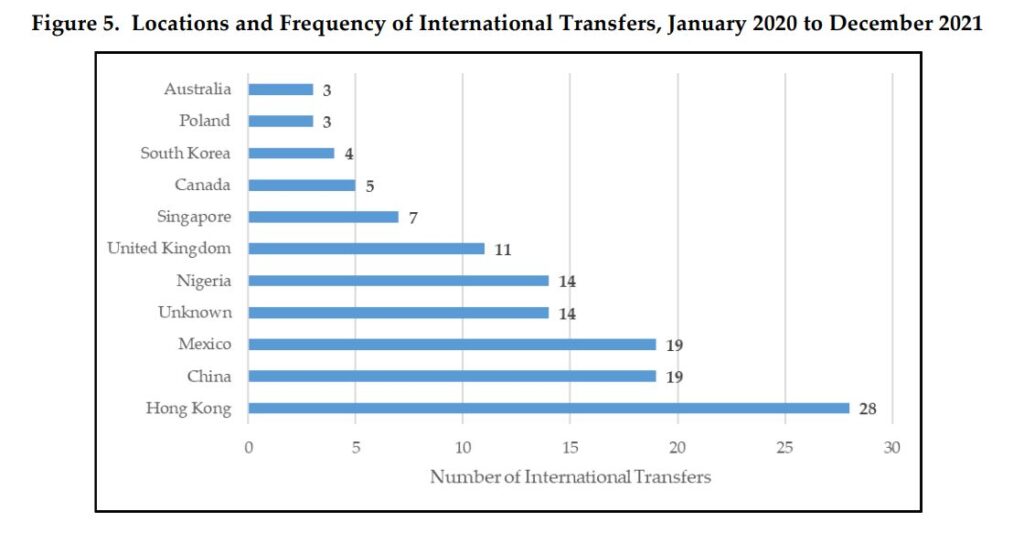
FinCEN reported that 88% of Real Estate Business Email Compromise incidents involved initial domestic transfers of funds to accounts at US depository institutions.
While the vast majority of initial fraudulent transfers went to US depository institutions, the fraudsters quickly move funds to secondary bank accounts, or online payment platforms, or to purchase Bitcoin.
The initial transfer of fraudulent funds went to international destinations about 8% of the time.
Want more Insights into FinCEN Data?
Evolution of 314(a) Law Enforcement Use
Cryptocurrency SARs: What do we Know?
Dynamic Securities Analytics, Inc. provides litigation consulting to help clients successfully navigate disputes involving securities, cryptocurrency, and money laundering.