I often use the term “crypto crime” when I write about illicit activity involving cryptocurrency. But what is crypto crime? And what information am I trying to convey by using the term crypto crime?
Why is it important to define crypto crime?
Crime statistics — such as victim complaints and dollars lost — are often categorized into various categories. The crime categories may be legal standards (i.e. firearms offenses in Chapter 44 of Title 18 of the U.S. Code) or colloquially defined. The DOJ and other law enforcement agencies often organize teams around crime typologies (i.e. FBI Art Crime Team). A typology is a systematic grouping of a class or category around a common principle relevant to a particular analysis.
If we don’t define a crime category, then measuring and organizing efforts to combat the threat will be lacking.
The same crime can also be categorized several ways. For example, consider a scheme where the victim is told they need to pay an upfront “tax” to unlock a big windfall. Different folks looking at the crime might refer to it as…
- Criminologist = advance fee fraud
- Layperson = Nigerian prince scam
- Police = confidence scam
- Social worker = elder abuse
- IC3 = lottery / sweepstake / inheritance
- Technologist = cybercrime
- Prosecutor = property crime
None of the varying classifications are wrong and more than one can apply. How the crime is classified depends on the classifier’s viewpoint, experience, or the common principle relevant to a particular analysis.
There has been little attempt to clearly define crypto crime although the term is frequently used. Contrasting or conflicting definitions of crypto crime can lead to misunderstanding, and not defining crypto crime at all, will leave us less prepared to counter it.
Modeling Cybercrime Definition for Crypto Crime
Cybercrime is another category of crime but doesn’t have a universally agreed upon definition. The term cybercrime was so nebulous that in 2022, Congress passed the Better Cybercrime Metrics Act which required the Department of Justice to develop definitions and categories for cybercrimes in its national crime reporting system.
The GAO defined cybercrime and cyber-enabled crime in its June 2023 report, “Cybercrime: Reporting Mechanisms Vary, and Agencies Face Challenges in Developing Metrics.”
“Cybercrime is a broad term that can refer to a variety of illegal activities that target potential victims online or make use of the internet to carry out illicit activities.”
Cyber-enabled crime: traditional criminal activities that are facilitated by the use of the internet
The GAO’s cybercrime definitions serve as a good starting point to understanding what is crypto crime.
Defining Crypto Crime
There are three types of illicit activity that I define as crypto crime:
- Illegal activities that target cryptocurrency.
- Illegal activities that make use of the features of cryptocurrency to carry out the illicit activity.
- Illegal activities that would occur much less frequently but for the ability to monetize the crime using cryptocurrency.
Considering the three categories of illicit activity and the GAO’s cybercrime definition, we see that crypto crime can be defined as:
Crypto crime: a variety of illegal activities that target cryptocurrency or make use of cryptocurrency to carry out illicit activities
While crypto-enabled crime can be defined as:
Crypto-enabled crime: traditional criminal activities that are facilitated by the use of cryptocurrency
1) Illegal activities that target cryptocurrency
Let’s examine the first category of crypto crime: a variety of illegal activities that target cryptocurrency.
Just as bank robbers target cash and jewelry thieves target gold and diamonds, some criminals target cryptocurrency. Illegal activities that target cryptocurrency include SIM-swapping to gain control of crypto wallets, a wrench attack, and hacks of crypto exchanges/ bridges / DEXs.
Crystal Blockchain prepared a list of the largest crypto thefts from June 2011 through March 2024. The list included $6 billion stolen in 220 security breaches and another $5B stolen in 345 DeFi hacks. By my definition, these breaches and hacks would all be considered crypto crimes since illegal activities targeted cryptocurrency.
2) Illegal activities that make use of the features of cryptocurrency to carry out illicit activities
Stepping away from crypto for a moment, let’s consider other crimes that make use of the specific features of a financial product to carry out illicit activities. Here’s a few examples: check-kiting, gift card draining, and securities fraud.
You cannot kite a check without a check (actually two checks). Check-kiting exploits the features (or bug) of checks, namely the delay between a customer presenting a check and the bank receiving funds. You cannot check kite with say a… debit card and a stack of $20 bills. The features of checks are necessary for the illicit activity to work.
Gift card draining requires access to and tampering with physical gift cards. When unsuspecting consumers buy and fund the gift cards, the funds instead go to the criminal. Gift card draining only works on physical gift cards. Scammers can’t instead place the tampered gift card code on a $10 bill and get the same results. The financial product– gift cards– is key to making this scheme work.
Securities fraud (involving real securities) takes many forms including insider trading, market manipulation and front-running. But in all of these cases, a security is needed to conduct the fraud. You can’t insider trade an ACH deposit, or front-run a debit card.
Now let’s circle back to crimes that make use of the features of cryptocurrency.
Cryptocurrency is attractive to bad actors because it has so many of the features they value in a financial product. Blockchain-based cryptocurrency transactions can move funds: far, fast, in large amounts, irreversibly, anonymously, and to a third-party. Bad actor also make use of how new crypto tokens are created and how transactions are added to a blockchain.
There are a variety of crimes that make use of the features of cryptocurrency, in which another financial product cannot be substituted to execute the crime.
Here are a few examples:
Address Poisoning is when a bad actor sends small amounts of crypto to victims from addresses that mimic legitimate addresses that the victim has interacted with, in the hope that the victim will send crypto to the copycat address. If a bad actor placed the malign wallet address on a gift card or a check, nothing would happen. This crime can only happen with crypto.
Cryptojacking. Cryptojacking makes use of how new crypto is created. New cryptos are created by “mining” which uses computing power to solve complex problems. Purchasing and powering the computers is costly, so bad actors install malware on other people’s computers but send the newly created crypto to themselves. You cannot cryptojack your way into creating a new municipal bond.
Hacks. Crypto hacks are different from hacks of other financial products. A crypto hack / theft does not require the involvement of a financial intermediary. If a bad actor gains control of the private keys (or enough ‘votes’ in a DAO) they can transfer the crypto to their own wallet. In contrast, if a bank account is hacked, the hacker moves the funds to another financial institution.
A bank, in its role as an intermediary, may:
- prevent logins from an unknown IP address, or unusual location, or
- hold a transaction if the transaction is out of pattern for the customer, or
- prevent and report an attempted transaction to a sanctioned entity.
There is no equivalent in blockchain-based crypto transactions. Bad actors exploit blockchain features such as decentralization (no intermediary) and immutability (irreversibility) to execute crypto hacks.
Some commentators argue that blockchain transparency makes cryptocurrency ill-suited for illicit finance. However, only a sliver of cryptocurrency transactions is recorded on the blockchain. Most cryptocurrency transactions (including stablecoin transactions) occur within cryptocurrency exchanges which have varying degrees of compliance with AML laws.
Illegal activities targeting or making use of the features of cryptocurrency that occurs within or by cryptocurrency exchanges are included in my definition of crypto crime.

Other crypto crimes that make use of the features of cryptocurrency include “infinite mints” or 51% attacks.
Certainly, some crypto crimes have a non-crypto analogous counterpart. For example, address poisoning is similar in some ways to Business Email Compromise. But if you airdropped a fake bank routing number to a crypto wallet, nothing would happen.
For those reading closely, some crypto crimes may be categorized as both illegal activities targeting crypto and illegal activities relying on the features of crypto.
There’s No Such Thing…
When someone asserts that, “there’s no such thing as crypto crime, there’s just fraud or theft” they are ignoring the fact that bad actors intentionally exploit the features of cryptocurrency to execute schemes, and that some crypto crimes specifically target crypto holdings.
Crypto crime is not merely using cryptocurrency as the means of value transfer in the commission of a crime — that scenario more closely aligns with the definition of crypto-enabled crime. Crypto crime is when cryptocurrency is the target of the crime or the means by which the crime is executed. For crypto crimes like DeFi hacks and address poisoning, it wasn’t as if the bad actor flipped a coin– heads they use crypto, tails they use certificates of deposit.
At best, folks stating “there is no such thing as crypto crime” are trying to convey that law enforcement shouldn’t be intimidated by cryptocurrency and/or that cryptocurrency is so ubiquitous in illicit activity that it is futile to separate it out. Following that line of thinking, then we should toss the terms “cybercrime” and “elder abuse” in the dustbin.
In addition, less well-intentioned individuals have co-opted “there is no such thing as crypto crime” to gaslight the public and lawmakers about the real harms from crypto crime.
3) Illegal activities that would occur much less frequently but for the ability to monetize the crime using cryptocurrency
I consider certain crimes that were previously non-monetizable to be crypto crimes because but for the ability to monetize the crime using the features of cryptocurrency, those crimes would occur much less frequently.
Commercial child sexual abuse material (CSAM), financially motivated sextortion of minors, and ransomware all fit the bill of crypto crimes by this definition. I’ll explain more using commercial CSAM and financially motivated sextortion as examples.
Commercial CSAM
Child sexual abuse material (CSAM) has existed online for decades. Yet, it was not until the introduction of cryptocurrency as a means of payment did the production and sale of CSAM become an increasingly commercial activity.
The commercialization of online child sexual abuse material required methods to anonymize participants’ (1) involvement in producing and/or consuming CSAM, and (2) payments. The internet, in conjunction with Tor and end-to-end encrypted messaging, solved the first issue. Cryptocurrency solved the latter.
“Bitcoin has been used to monetize the production of child exploitation material—a development rarely seen before the rise of cryptocurrency.”
– U.S. Department of Justice
Financially Motivated Sextortion of Minors
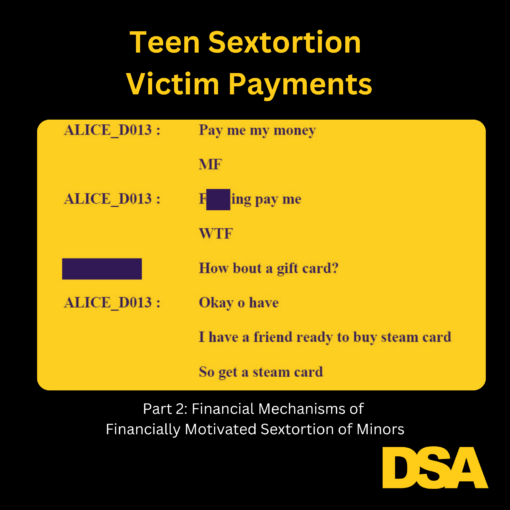
Financially motivated sextortion offenders often connect with teenage male victims through social media, online games, and messaging apps by creating profiles that appear to be young women. While posing as teenage girls, the predator secretly records explicit video calls with children or asks them to send sexually explicit pictures. After receiving sexually explicit content from a child, the offender threatens to release the material to friends, family, schoolmates, and/or social media followers unless the victim provides payment.
Financially motivated sextortion of children has developed a standard operating procedure for financial flows.
- Demand and receive payment from victims via P2P payments or gift cards
- Use money mules to pool extorted funds in U.S.-based payment apps
- Purchase bitcoin with the victims’ funds from US-based crypto exchanges. These crypto exchanges also often have an associated payment app.
- Transfer the bitcoin to overseas perpetrators using an international crypto exchange.
Financially motivated sextortion of minors is a rapidly growing threat that relies on cryptocurrency to remit profits across international borders.
4) Crypto-enabled crime
A variety of traditional crimes are facilitated by cryptocurrency including drug trafficking, prostitution, espionage, and corruption. For example, when drugs are traded on a dark web marketplace amongst anonymous participants for cryptocurrency, these illegal activities are crypto-enabled crimes. However, if crypto disappeared tomorrow, traditional crimes such as drug trafficking would still exist and probably exist at the same level as today.
I don’t think the same can be said for ransomware, commercial CSAM, financially motivated sextortion, or even pig butchering (crypto-enabled romance scams). These crimes would likely decrease if the ability to monetize them is hindered.
Information Conveyed by “Crypto Crime”
When I use the term crypto crime, I am emphasizing cryptocurrency as the commonality that is of interest to me. Similarly, a social worker might focus on the victim’s age and classify crimes as “elder abuse” or “internet crimes against children.”
Data on illegal activities targeting, using and/or facilitated by cryptocurrency is often incomplete, limited to on-chain data, or lumped in with other typologies. A clear definition of crypto crime and crypto-enabled crime will allow for better measurement, analysis, and countering of the threat posed by illegal activities targeting, using or facilitated by cryptocurrency.
As I recommended to Congress:
- FinCEN should regularly publish the number of cryptocurrency-related SARs.
- The SAR form should be updated to include cryptocurrency as a financial product/instrument.
- The SAR form should be updated to specifically categorize SARs filed by cryptocurrency-related institutions (VASPs).
_____________________________________
Want more Cryptocurrency Insights?
The Limits of Blockchain Transparency: Fraud with Crypto Companies
Cryptocurrency Traceability: Unraveling Underlying Assumptions
3 Misconceptions About Cryptocurrency Crime Estimates